Bank logs spamming is a rewarding yet demanding task. If you learn how to correctly acquire logs at scale, you will be able to sell and use them for black-hat use cases. In this essay, I’ll show you how to correctly spam Bank Logs.
How to Spam for Bank Logs in 2024?
To spam for Bank Logs, you must first create a phishing website that deceives users into believing it is real and then submits their information using that fallacy. You must collect the bank logs from the phishing website’s backend, do a background check, and then log in to their bank accounts using the information you have obtained. This must all be accomplished quickly, as you do not want them to find out when you are active in the account.
Always use your VPN when phishing and retrieving data, as your digital footprint might be monitored if you do not use proper security precautions.
Let me give you a quick check list in order to complete the spamming operation.
We use email and SMS to deliver false pages (phished pages) to targets, making them believe they are logging into their genuine bank account when they click the messages. The data will include all of the information that customers typically submit when logging into their bank accounts, such as their bank account username, password, and login email address. The data we collect from these individuals is intrinsically “Bank Logs” because, once the bank log phishing page has acquired all of this information, their accounts can be accessed remotely for harmful purposes.
The phishing website is an exact replica of the real banking login interfaces used by actual banks. The code is simply swapped out and used on a false page created by you with a similar domain name, so the user has no idea it’s a fake.
Necessities for Bank Logs Spamming
To start spamming, you’ll need a few tools, which we’ll go over in this tutorial.
Using VPN while Phishing for Security Purposes
VPNs, or “Virtual Private Networks,” will disguise all of your spamming-related activities from top to bottom. Your real IP address will not be associated with any of the hacking operations, making it hard for government enforcement to trace it back to you. I recommend that you use a VPN at all times when setting up and running spamming activities. If you want to learn more about cashapp carding, we have a section on our website.
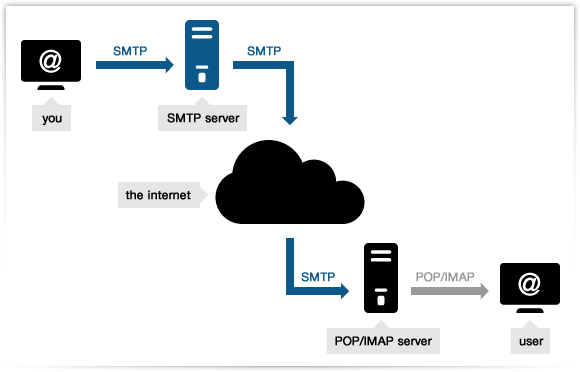
SMTP (Simple Mail Transfer Protocol)
Did you know that if a specific email account sends out too many emails that are reported to internal email provider systems, the account will be blacklisted/banned? When you spam for logs, you are emailing thousands of potential targets, waiting for them to convert.
Many of them could potentially report your email address. Having SMTP will help to mitigate this problem and prevent your email addresses from reaching their primary mailbox. Without SMTP in your plan, you will be unable to scale your operations, thus maintain it in your toolset.
SUTS (Spamming Using Text Scripts)
You must include a message in your email or text message to possible targets. Without a spamming text script, you won’t be able to persuade them that the message is legitimate. Text scripts generally strive to sound like what real banks would say.
The scripts must have a sense of “utility,” which means that when the user gets the email script, they feel compelled to make some sort of update or micro-optimisation to their bank account in the following days, or their account will be in a state of difficulty. An example is a script like “Your bank account has suspicious transactions. Please login to resolve.” , scripts like these promotes the aspect of urgency and lifts your conversion levels.
Creating Email List
The next item you’ll need in your toolkit is a list of emails to spam. These emails cannot be generated indiscriminately; they must be high-quality and genuine. Fortunately, there is an abundance of websites that sell and distribute real users’ email addresses. There are numerous more ways to locate live email addresses, such as employing hackers to penetrate firms’ databases and retrieve emails from them. I recommend that you perform your own study on how you want to collect emails.
Don’t use email generators or other fake forms of getting emails; your phishing messages will never convert and will be intrinsically worthless.
To grow your email list, use Facebook advertising to encourage users to sign up for offers. Then, use those emails to conduct spam campaigns.
Hosting 1:1 Cloned Pages
As previously stated, a “Cloned Page” is essentially a webpage that looks like the login portals used by genuine banks when people log in.
The users will enter their login information on these cloned sites, which will subsequently be routed to you. The webpage’s purpose is to serve as your principal phishing site once their emails have been flooded.
After you send the email to these users, a certain percentage of them will click on it. We call this the “click-through rate”; if they do not click on your email with the cloned page, they did not click through, and this will be deducted from the total rate, and vice versa if they do click through.
This rate is critical, and you will have an accurate estimate of how much traffic your Cloned Page is receiving vs how many spammy emails you have sent out. This rate will be tracked via both email and SMS messages.
Spamming for Bank Logs
This next section of the essay will go over the step-by-step process of carrying out the spamming operation from an operational standpoint, and it will be actionable by just following the procedures I’ll explain.
Where to Buy Bank Logs
In the past i use to spam all my bank logs, but now i get them from @AnonymousHelper01 on telegram . You can also buy from here
1.Build a compelling Phishing Page.
One of the most crucial things you should do before beginning the Phishing Page building process is to select the specific bank branch you want to create pages for. Go with the larger banks in the United States, such as Chase, Wells Fargo, and Capital One. This is because if the majority of Americans use one of these banks, the possibility of them clicking through it increases because they are more likely to do so at random.
The phishing clone page must be a 1:1 replica of the actual bank login portals; fortunately, there are pre-made templates where you can copy and paste the UI/UX and accompanying code. Once you’ve purchased these templates from dark web markets, you should begin putting the code and user interfaces on your website.
The second key feature of the phishing page that corresponds to the aesthetics of the cloned page is the domain. Domains increase the credibility of the phishing page’s appearance. The phishing page must resemble the real website, so the domain must be similar to the domain of the actual bank. For example, “capitalone.com” is a real banking website; a fake domain you could use would be “capitaIone.com” if you can’t tell the difference, except for the “L” in “Capital” in the real one; I used a capital “i” instead.
While many of these domains are already taken, with enough effort, you will be able to create website domains that are surprisingly similar yet may be somewhat different. The differences can be significant, and users may be less intelligent than you believe.

2. Purchase Secure Web Hosting for Phishing Pages
You should select a web hosting platform that will not block your domain if they discover you are purchasing names for nefarious purposes.
I would recommend any and all hosting platforms that only accept bitcoin for domain purchases. These site hosting platforms are less concerned with blackout consumers than others.
3. Execute Spamming Operation
As previously said, spamming emails must be familiar to the recipients. This means that your script must be 1:1 with the real banks, your phishing website must be customised with a good-looking URL, and your SMTP must be reliable enough to avoid ending up in spam folders.
Using Your Bait to Effectively Phish Targets
Your click-through rate will not always be high. In fact, less than 30% of people who receive your spam emails will ever open them. This is not a problem because if only half of the 30% of individuals who read your spamming email filled out their information, a thousand people would be spammed. That’s 300 people that read your email, and if 150 of them filled out their information, the average value of a bank log on the black market is $200.00, so 150 times $200 equals $30,000 in profit. This assumes you aren’t only using the logs for yourself, which would result in higher profits if cashed out.
Sustaining Phishing Operational Perpetuity
Redundancies may emerge as a result of decreasing click-through rates or a host terminating your domain. Staying ahead of these challenges can mean the difference between your spamming operation lasting a few weeks or a lifetime.
Acquire a full-stack crew to avoid redundancies and keep your operations running smoothly.
Conclusion
When you understand spamming, you will immediately realise that it is by far one of the most profitable sectors in the blackhat world after you have achieved proficiency. Hearing about it is one thing; doing it is another.
I recommend that you practise till you observe positive results. Once you observe results, quickly expand your operation and hire a team. You won’t even need to cash out the logs yourself, so you can easily sell them on the underground market and turn into a money machine.
Good luck on your journey
Bank logs, Spamming tutorial, Latest tutorial, Online fraud techniques, Cybersecurity tips, Hacking financial accounts, Unauthorized access, Phishing methods, Carding procedures, Dark web transactions, Money laundering guide, Identity theft prevention, Digital security measures, Anti-fraud measures, Protecting personal information, Fraudulent activities online, Scam avoidance tactics, Secure online banking, Digital privacy tips, Financial cyber threats, Risk mitigation strategies, Secure transaction practices, Account protection tips, Banking security protocols, Fraud detection methods
Looking for a Reliable Vendor for CC, Banklogins and Instant Transfer Vendor Then Click the Link Below
Visit: Cardinghub.com
Contact Us: Click Here
Shop link: Click Here



